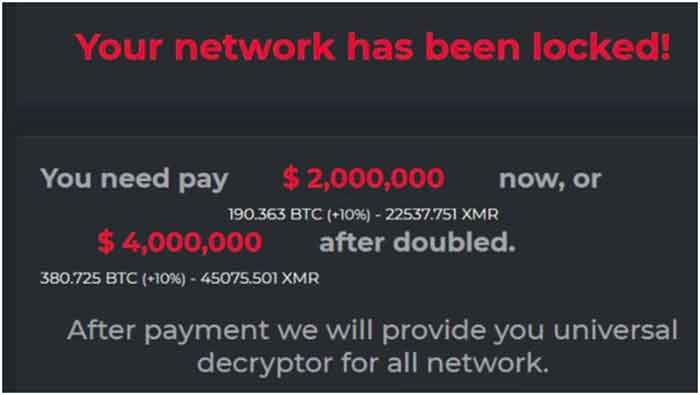
An example of a DarkSide ransomware notice that appears on victims’ computer screens
The U.S. government has issued emergency legislation on Sunday after the Colonial Pipeline, the country’s largest fuel pipeline, was hit by a ransomware cyber-attack.
The Colonial Pipeline carries 2.5 million barrels a day, 45% of the U.S. East Coast’s supply of diesel, gasoline and jet fuel.
It was completely knocked offline by a cyber-criminal gang on Friday and is still working to restore service.
The emergency status relaxes rules on fuel being transported by road.
It means drivers in 18 states can work extra or more flexible hours when transporting gasoline, diesel, jet fuel and other refined petroleum products.
The states are Alabama, Arkansas, District of Columbia, Delaware, Florida, Georgia, Kentucky, Louisiana, Maryland, Mississippi, New Jersey, New York, North Carolina, Pennsylvania, South Carolina, Tennessee, Texas and Virginia.
The Colonial Pipeline, said in a vaguely worded statement late Friday that it had shut down its 5,500 miles of pipeline in an effort to contain the breach.
Earlier Friday, there were disruptions along the pipeline, but it was not clear at the time whether that was a direct result of the attack or of the company’s moves to proactively halt it.
Experts say fuel prices are likely to rise 2-3% on Monday, but the impact will be far worse if it goes on for much longer.
With a lot of fuel now stranded at refineries in Texas, there is a big trouble waiting. The first areas to be impacted would be Atlanta and Tennessee, then the domino effect goes up to New York.
Oil futures traders were now “scrambling” to meet demand, at a time when U.S. inventories are declining, and demand, especially for vehicular fuels is on the rise as consumers return to the roads and the U.S. economy attempts to shake off the effects of the pandemic.
The temporary waiver issued by the U.S. Department of Transportation enables oil products to be shipped in tankers up to New York, but this would not be anywhere near enough to match the pipeline’s capacity.
Multiple sources have confirmed that DarkSide, a cyber-criminal gang, infiltrated Colonial’s network on Thursday and took almost 100GB of data hostage, caused the ransomware attack.
After seizing the data, the hackers locked the data on some computers and servers, demanding a ransom on Friday. If it is not paid, they are threatening to leak it onto the internet.
Colonial said it is working with law enforcement, cyber-security experts and the Department of Energy to restore service.
On Sunday evening it said that although its four mainlines remain offline, some smaller lateral lines between terminals and delivery points are now operational.
While DarkSide is not the largest, such gang in this space, the incident highlights the increasing risk ransomware is posing to critical national industrial infrastructure, not just businesses.
It also marks the rise of an insidious criminal IT eco-system worth tens of millions of pounds that is unlike anything the cyber-security industry has ever seen before.
In addition to a notice on their computer screens, victims of a DarkSide attack receive an information pack informing them that their computers and servers are encrypted.
The gang lists all the types of data it has stolen, and sends victims the URL of a “personal leak page” where the data is already loaded, waiting to be automatically published, should the company or organization not pay before the deadline is up.
DarkSide also tells victims it will provide proof of the data it has obtained, and is prepared to delete all of it from the victim’s network.
According to Digital Shadows, a London-based cyber-security firm that tracks global cyber-criminal groups to help enterprises limit their exposure online, DarkSide operates like a business.
The gang develops the software used to encrypt and steal data, then trains up “affiliates,” who receive a toolkit containing the software, a template ransomware demand email, and training on how to carry out attacks.
The affiliate cyber-criminals then pay DarkSide a percentage of their earnings from any successful ransomware attacks.
And when it released a new software in March that could encrypt data faster than before, the gang issued a press release and invited journalists to interview it.
The gang even has a website on the dark web where it brags about its work in detail, listing all the companies it has hacked and what was stolen, and an “ethics” page where it says which organizations it will not attack.
It also works with “access brokers” – nefarious hackers who work to harvest the login details for as many working user accounts on various services as they can find.
Rather than break into these accounts and alert users or the service providers, these brokers sit on the usernames and passwords and sell them off to the highest bidders – cyber-criminal gangs who want to use them to carry out much larger crimes.
Digital Shadows thinks the Colonial Pipeline cyber-attack has come about due to the coronavirus pandemic – the rise of engineers remotely accessing control systems for the pipeline from home.
James Chappell, co-founder and chief innovation officer at Digital Shadows, believes DarkSide bought account login details relating to remote desktop software like TeamViewer and Microsoft Remote Desktop.
He says it is possible for anyone to look up the login portals for computers connected to the internet on search engines like Shodan, and then “have-a-go” hackers just keep trying usernames and passwords until they get some to work.
“We’re seeing a lot of victims now, this is seriously a big problem now,” said Chappell.
“Every day there’s new victims. The amount of small businesses that are falling victim to this, it is becoming a big problem for the economy globally.”
The Colonial Pipeline said it had shut the pipeline itself, a precautionary act, apparently for fear that the hackers might have obtained information that would enable them to attack susceptible parts of the pipeline.
Administration officials said they believed the attack was the act of a criminal group, rather than a nation seeking to disrupt critical infrastructure in the U.S. But at times, such groups have had loose affiliations with foreign intelligence agencies and have operated on their behalf.
In recent months the frequency and sophistication of ransomware attacks have soared in the U.S., crippling victims as varied as the District of Columbia police department, hospitals treating coronavirus patients and manufacturers, which frequently try to hide the attacks out of embarrassment that their systems were pierced.
Colonial, which is privately held, declined to say whether it planned to pay the ransom, which frequently suggests that a company is considering doing so, or has already paid. Nor did it say when normal operations would resume.
Colonial’s pipeline transports refined gasoline, diesel fuel and jet fuel from the Gulf Coast up to New York Harbor and New York’s major airports.
People familiar with the cyber-attack investigation said that although Colonial insisted that it became aware of the attack on Friday, the events appeared to have unfolded over several days. It has hired the private cybersecurity company FireEye, which has responded to the hacking of Sony Pictures Entertainment, energy facility breaches in the Middle East and many events involving the federal government.
The incident opens the question of whether the attackers themselves now had the ability to directly turn the pipelines on or off or bring about operations that could cause an accident.
The ransomware attack is the second known such incident aimed at a pipeline operator. Last year, the Cybersecurity and Infrastructure Security Agency reported a ransomware attack on a natural gas compression facility belonging to a pipeline operator. That caused a shutdown of the facility for two days, though the agency never revealed the company’s name.
Cybersecurity experts say the rise of automated attack tools and payment of ransom in cryptocurrencies, which make it harder to trace perpetrators, have exacerbated such attacks.
Colonial Pipeline, based in Alpharetta, Ga., is owned by several American and foreign companies and investment firms, including Koch Industries and Royal Dutch Shell. The pipeline connects Houston and the Port of New York and New Jersey and provides jet fuel to major airports, including those in Atlanta and the Washington, D.C., area.
So far the effect on fuel prices has been small, with gasoline and diesel futures rising about 1 percent on the New York Mercantile Exchange on Friday. On average, prices for regular gasoline at the pump in New York State rose on Saturday by a penny, to $3 per gallon from $2.99. Over the past week, gasoline prices have risen nationwide by 6 cents per gallon, according to the AAA motor club, as global oil prices have risen rapidly.
Prices at the pump could be affected in different ways depending on the region. If there is a prolonged shutdown, areas from Alabama north through Baltimore will potentially see shortages. However, Midwestern and Ohio Valley states could actually benefit from cheaper shipments from the gulf refineries as the plants divert stranded supplies.
GET COUNTERCURRENTS DAILY NEWSLETTER STRAIGHT TO YOUR INBOX