China’s alleged cyber-attacks on Indian power facilities is the latest sensational story featured in the Indian media, print and electronic, not to speak of the wild social media.
For those who do not read the small print, it is taken for granted that the “wily Dragon” was, as usual, out to undermine India.
“Misinformation refers to false or out-of-context information that is presented as fact regardless of an intent to deceive. Disinformation is a type of Misinformation that is intentionally fals and intended to deceive or mislead.”
Both are promoted in a rampant manner, so as to manufacture consent …by ruling classes. Big Media is their handmaid in this.
We shall in this news analysis seek to expose how, in the Big Media, truth is the victim amid a maze of mis- and dis-information. And now there is a brazen attempt to muzzle the small but objective, online media outlets, like the Countercurrents.
Mumbai power outage on October 12, 2020, that lasted several hours, was attributed to China, based on a report by New York Times on Feb 28 , which cited a so-called “ study by Recorded Future, a Massachusettes-based outfit that studies the internet use by state actors…”
Times of India, Mar 2, 2021 reported that the NYT report was “to raise doubt Chinese state-backed hackers may have caused the October 12 power outage in Mumbai to warn India against strong pushback in the border row in Ladakh.”
The crux of the TOI report, rather a slanderous rumour, is this: it was a doubt:
“The report, however, said the study did not have sufficient evidence to substantiate this doubt.”
But it was sufficient to lit a prairie fire of anti-China venom in the India’s media jungle.
“ After Mumbai Power Blackout, Telangana Faces Cyber Attack Attempt by China,” said another report, india.com, March 3, 2021. And more such reports are likely.
China on March 1 rejected reports that Chinese hackers were behind the massive power outage that wiped out India’s financial capital Mumbai last year. But more about it later.
***
How was the Mumbai episode reported at that time and now?
indiatoday.in, 2020-11-20, had reported last year: “Mega Mumbai power outage may be result of cyber attack, final report awaited”
“A malware attack is suspected to be the reason behind Mumbai’s power outage last month. The case is being probed by the state’s cyber department and the final report is awaited,” it was reported. ..
Though sources in the Maharashtra cyber department stated that this was just a primary finding, a detailed report could be submitted to the state government in a week or so.
https://www.indiatoday.in/india/story/mumbai-power-outage-malware-attack-1742538-2020-11-20
The “detailed report expected in a week or so” apparently never came.
Indian media has no regular habit of pursuing a story, let alone independent investigation. It is overtaken with ever new fed news, ever new concoctions, blown up for TRP ratings, curiously adding background music to plain news, to make it sensational.
After years of such sensational and jingoistic stories, Republic TV and Arnab Goswamy are seeking to cover up their misdeeds, manipulation and doctoring of TRP ratings. But the show goes on, even as the Union Govt is thinking of gagging the web magazines etc that are a little sober and factual.
The report now : indiatoday.in, March 2, 2021, reported, again fed news:
Maharashtra Energy Minister Nitin Raut confirmed a Chinese conspiracy behind the October power outage in Mumbai…”There is truth in the claims made by NYT. We had formed three committees to inquire into the matter. We will receive a detailed report from the cyber department but based on the preliminary information I have, there definitely was a cyber attack and it was a sabotage,” Nitin Raut said.
On October 12, 2020, a grid failure in Mumbai resulted in a massive power outage, stopping trains on tracks, hampering those working from home amidst the Covid-19 pandemic and hitting the economic activity hard.
Almost five months later, now, the Minister inspired by NYT report of Feb 28, says a detailed report is still awaited. But he “confirmed a Chinese conspiracy.”
It is notable that the Maharashtra government is presently led by the jingoistic Shiv sena in alliance with Rahul-led Congress out to question Modi’s “guts” in facing upto China. That was what BJP did when Congress made truce with China after some sabre-rattling.
“There isn’t enough evidence”, but a Minister “confirmed a Chinese conspiracy”
Let us see some fine print in the report by indiatoday.in, March 1, 2021.
“China cyberattack on India could have led to Mumbai power outage last year, says NYT report”
That is the title of the report which reads as follows:
Cybersecurity company, Recorded Future, notified the Indian government about the China-linked threat activity group, RedEcho, which may have been responsible for the Mumbai power outage.
HIGHLIGHTS
- Mumbai faced a massive power outage on October 12, 2020.
- Earlier reports hinted about a possible cybersecurity attack that caused the outage.
- A new report says the China-linked threat activity group, RedEcho, may have been responsible.
Then we see some extracts:
- The NYT report says that the malware tracing was done by Recorded Future, a cybersecurity company founded in 2009 with headquarters in Somerville, Massachusetts.
- The company claims that most of the malware was not activated, which may mean that a small proportion of malware caused the Mumbai power outage.
- However, the report adds that the cybersecurity company couldn’t examine the code itself because of the restrictions, which meant it could not get inside India’s power systems. The report says that the cybersecurity company notified Indian authorities.
A crucial part of the report says:
- The cybersecurity company does point that despite some overlaps with previous groups, there isn’t enough evidence to attribute the Mumbai power outage to an existing hacker group. However, it will “continue to track it as a closely related but distinct activity group, RedEcho.”
- The cybersecurity company says it has sent its findings to Indian Computer Emergency Response Team (or CERT-In) within the Ministry of Electronics and Information Technology of the Government of India.
- It adds that the government has acknowledged the receipt twice, though there has been no confirmation of the fact that the code infected in the power grid may have any links with China-based hackers.
*** ***
“Mumbai blackout: Government denies China’s cyber campaign against Indian power grid”
That is the title of a report by timesofindia.com, Mar 1, 2021:
A study conducted by a US-based company had suggested that a China-linked group targeted India’s power grid system through malware.
India on March 1 said there is no impact on operations of Power System Operation Corporation (POSOCO) due to any malware attack and that prompt actions are taken on advisories issued against such threats.
But Maharashtra Minister makes assertions:
“October 2020 blackout could be cyber sabotage: Maharashtra minister”
Contrary to the Union power ministry statement, Maharashtra home minister Anil Deshmukh said that the massive power outage in Mumbai last October was an attempt at “cyber-sabotage” according to a preliminary report.
Addressing reporters in Mumbai, Deshmukh said Maharashtra Cyber Cell has submitted a preliminary report which suggests that the grid failure in Mumbai on October 12 last year was likely to be a cyber sabotage.
Mumbai faced a massive power outage last year, on October 12, 2020. But till date, there are no independent reports by Indian sources, official or unofficial. Govt agencies make comments on and after NYT report of Feb 28.
Delhi has been fretting and fuming against China for almost an year now, on LAC etc. But what does it say about this issue?
The ministry of power responding to the findings of the study, said, “There is no impact on any of the functionalities carried out by POSOCO due to the referred threat. No data breach/ data loss has been detected due to these incidents.”
While the study raised suspicion whether the massive power outage in Mumbai in October 2020 was a result of the online intrusion, the ministry did not mention the Mumbai outage in its statement.
Other malware was reported in November; due action taken: Power ministry
In its report, Recorded Future notified the appropriate Indian government departments prior to publication of the suspected intrusions to support incident response and remediation investigations within the impacted organisations.
The ministry explained in its statement, “The IPs mentioned in Red Echo related advisory are matching with those given in Shadow pad Incidents already informed by CERT-in in the month of November 2020. Matching, but…
“ Observations from all RLDCs (regional load dispatch centres) & NLDC (national load dispatch centre) shows that there is no communication & data transfer taking place to the IPs mentioned.”
All IPs and domains listed in NCIIPC mail have been blocked in the firewall at all control centres.
“ Accordingly, action has been taken to address these threats.”
India is said to be a great soft power, with huge and highly talented IT and allied services, including cyber security. But there are no independent studies and reports from Indian sources, despite power outage last October. It depends on news fed by vested interests.
Domestic political rivalries, particularly between the Union and the Maharashtra governments, taint and confound the issues. To what extent they go was seen in Sushant Singh Rajput and Kangana Ranaut affairs, and in Republic media TRP manipulations case. Same is the case with the alleged cyber attacks.
Union govt agencies denied…but rumor mill is active.
*** ***
China too denied and put things in perspective
The Chinese embassy in India on March 2 firmly opposed Indian media’s allegation of cyberattacks from Chinese hackers on Indian facilities.
“The relevant allegations are pure rumors and slanders,” said a spokesperson of the Chinese embassy in response to a query on some Indian media’s quoting Western media as saying that Chinese hackers may have launched cyberattacks on India’s power system, ports and two vaccine companies.
“Cyberattacks are highly complicated and sensitive, and their origin is difficult to trace. Speculation and fabrication have no role to play on the issue of cyberattacks. It is highly irresponsible to accuse a particular party when there is no evidence,” the spokesperson said. “China is firmly opposed to such irresponsible and ill-intentioned practice.”
The investigators who wrote the Recorded Future study, NYT Report said, that “the alleged link between the outage and the discovery of the unspecified malware” in the system “remains unsubstantiated.” “It found that most of the malware was never activated…”
There are other reports that indicated the origin was from Taiwan, South korea, and others, apart from US itself.
Origin is difficult to trace, said china. What is the technical view? See below:
*** ***
IBM explains how the Origin of a cyber attack is clouded and confounded
Technically and typically cyber attacks are disguised and mislead and confound the real source or origin of the attack.
In an article, What is a cyber attack? IBM Services , 1 December 2020, explained:
“ Smurf attack: Techopedia notes that Smurf attackers apply some common facts about IP and Internet Control Message Protocol (ICMP) when attacking. Notably, the fact is that “ICMP is used by network administrators to exchange information about network state and can also be used to ping other nodes to determine their operational status.”
“To better understand how a Smurf attack works, you need to know what “spoofing” is. Spoofing occurs when a communication from an unknown source is disguised to seem like it comes from a known or reliable source. Spoofing is also used by cyber criminals for man-in-the-middle and similar cyber attacks.
“What does a Smurf attack target? The attacker sends ICMP echo requests, a “ping” to the broadcast network address, also known as IP address, or addresses being targeted. All the ICMP pings are sent from a spoofed address that’s meant for the intended victim. These ICMP echo requests are broadcast out to other addresses. These addresses respond back to the actual address that the attacker was spoofing.
“ What’s the result of a Smurf attack? The vast amount of ICMP echo requests and pings barrage the victim’s network with high computer network traffic. This flood of echoes and pings drains the bandwidth of the victim’s network and causes the victim’s server to crash.
“What’s scary about Smurf attacks? They can be automated and the process is repeatable, making Smurf attacks capable of incredible disruption.”
ps://www.ibm.com/services/business-continuity/cyber-attack
*** ***
“Both China and India are contributors to international cooperation on vaccines, and both have fallen victim to disinformation”: China
“Repeated allegations to discredit China are only a means of survival for those military industrial enterprises”
“Western media is trying to create new bad blood over the vaccine issue between China and India at a time when two sides are pushing for the disengagement of border troops, and the practice is pure evil slanders, observers said.” (globaltimes)
Thus China puts in perspective. The NYT report’s timing is significant: amid vaccine wars and disengagement.
Noting that for some time there had been certain speculation about China’s so-called theft of other countries’ vaccines through hacker attacks, China’s spokesperson said China takes the lead in vaccine research and development, and does not need to and will not rely on “stealing” to obtain vaccines.
“Both China and India are contributors to international cooperation on vaccines, and both have fallen victim to disinformation,” said the spokesperson. “This is not in the common interests of the international community.”
“We are firmly opposed to politicizing and stigmatizing cybersecurity issues, which is not conducive to resolving hacking issues and will only weaken mutual trust among countries,” said the spokesperson, urging relevant media to deny such groundless disinformation platforms and channels for dissemination.
China, as a staunch defender of cybersecurity and also a major victim of hacking and cyberattacks, firmly opposes and combats all forms of cyberattacks and crimes, the spokesperson said.
“Cyberattacks are a challenge faced by all countries,” said the spokesperson. “China calls on all countries to advance dialogue and cooperation and handle this challenge together on the basis of mutual respect, equality and mutual benefit.”
“China is ready to work with other parties to jointly address cybersecurity threats, safeguard peace and stability in cyberspace and build a community with a shared future in cyberspace,” the spokesperson said.
(Xinhua| 2021-03-02)
It is notable that despite such formal policies and official clarifications, media continued jingoistic propaganda and provocative visuals. Is this media freedom, as practised by the ruling elite?
If some facts are reported, Rahul Gandhi tweets, as last year he alleged: “The media is muzzled and terrified. The truth seems dormant. But it flows in the blood of every single Indian army officer and soldier. They know exactly what is happening in Ladakh…”
There is competitive nationalism and jingoism, oneupmanship, but not truth…falsehood is what is valued: Asatyameva Jayate! Long Live Falsehood.
Is china’s contention far-fetched? Let us see the vaccine wars.
*** ***
Vaccine wars: Presidents and prime ministers act as salesmen of vaccines
The whole issue got blown up in the context of business rivalries regarding Covid vaccines. Presidents and prime ministers are acting as salesmen of vaccine business, now worth billions, which is valuable in the light of economic crisis that got aggravated by Covid-19 shutdowns.
Accusations were made, mutually, about theft of data and technologies even as efforts were made, by states as well as corporations, to push into markets vaccines that are not duly tested and certified.
Western agencies indulged in misinformation and disinformation.
Even UK and EU got involved in Spectre of vaccine trade war between Britain and EU, as was the title of a report by the guardian.com, Jan 28, 2021:
EU Health Commissioner, Stella Kiriakides “rejected the logic of first come first served…that may work in a butcher’s shop.” Such is the bitterness where the imperialists turned into Shylocks.
“The clash was after an year of tense negotiations over post-Brexit trade and security” the report said, indicating how they got meshed up.
It was around Oxford-AstraZeneca vaccine that is also being pushed by India.
If that is bitterness between two western imperialist entities, one can only imagine how they would besmirch and damn China, a challenger in trade, politics and ideology.
Dirty games of Anglo-American imperialists
The slander mongers, who combined cyber attacks and vaccine wars, are all related to Anglo-American imperialists: It is Reuters and NYT, their media majors, who reported in the main.
They cited Cyfirma boss NRI Kumar Ritesh, top cyber official who is with British intelligence agency MI6. Cyfirma is Goldman Sachs-backed, ie., US Inc backed.
They also cited BAE, a British MNC dealing in arms and security. It operates from UK and US, and is one of the six largest suppliers to US Defence department.
It is this unholy alliance manipulating facts, concocting stories and telling half truths full of “may haves” etc conceding they are “unsubstantiated” .
It is at a time the MNCs are engaged in a trade war around the Covid-19 vaccines.
It was in such a context that Reuters reported on March 1 that a Chinese hacking group called APT-10, or Stone Panda, had identified gaps and vulnerabilities in the IT infrastructure and supply chain software of Bharat Biotech and Serum Institute of India (SII), the world’s largest vaccine maker. But it did not spell out a clear connection between the so-called hacker group and the Chinese government.
The Reuters report went even further in its attempt to find logical grounds for the alleged Chinese government-backed hacking event by citing Cyfirma boss Kumar Ritesh, a top cyber official with British intelligence agency MI6, as saying, “The real motivation here is actually exfiltrating intellectual property and getting competitive advantage over Indian pharmaceutical companies.”
Chinese Embassy in India and the country’s cyber-security insiders have refuted a Reuters report which cited Goldman Sachs-backed cyber intelligence firm Cyfirma on March 1 as claiming that a “Chinese state-backed’ hacking group had attacked two Indian vaccine makers in recent weeks, slamming such groundless allegations to be nothing but an ill-indented slander and stressing that China leads in the vaccine research and development and there is no need for China to rely on “stealing” to obtain vaccines.
Refuting the Reuters report, a spokesperson with the Chinese Embassy in India on Match 2 via its official WeChat public account criticized the “irresponsible, ill-intended smearing acts”, and said China firmly opposes politicizing cyber-security issues.
“The relevant allegations are pure slander. Since it is highly complicated and sensitive to figure out the origins of cyber attacks, one should not target a specific party to blame it when there is no evidence,” the spokesperson noted.
Significantly, China made friendly references to India, unlike the hostile commentaries by Indian big media, aided and abetted by US agencies:
“China takes the lead in vaccine research and development, we don’t need to and will not rely on ‘stealing’ to obtain vaccines. Both China and India are contributors to international cooperation on vaccines, and both have fallen victim to disinformation. This is not in the common interests of the international community,” the spokesperson added.
Cyfirma did not respond to the Global Times’ request for comments.
Chinese cybersecurity insiders told the Global Times that they have no idea of this so-called hacker group, and are not surprised by this round of accusations made by Western media using the same old trick of tarnishing China with the cybersecurity issue.
Qin An, director of the China Internet Space Research Institute, told the Global Times that the allegations that APT10 had links with the Chinese government are absolutely groundless, because the Chinese government has never supported cyberspace crime, as regulations and laws explicitly prohibit such acts.
Similarly, in 2017, APT10 was also targeted in a report by BAE systems, a British multinational arms, security, and aerospace company, for a series of intrusions against several major service providers.
Qin told the Global Times that the clear intention of this report by BAE systems was to hype up the cyberthreat posed by China.
When cyberspace was regarded as the second public sphere of war, US military industrial enterprises opted to transform themselves by acquiring cyberspace companies in order to obtain more funding from the government.
“The repeated allegations to discredit China are only a means of survival for those military industrial enterprises,” Qin said.
There has been never solid evidence to prove that China has supported any hacker groups including APT-10, and the Western media’s accusation also acknowledged that.
(https://www.globaltimes.cn/page/202103/1217143.shtml)
We had seen last year how India and China co-operated, helping each other, with mutual supplies of medicines and equipment in early phases of Covid-19. All that was turned into bitter hostility within weeks, amid stories of disinformation. The screen play is similar whether it is fictional films or hard news.
Also last week, refuting reports that China had initiated cyberattacks (against India’s power grid resulting in massive power outages) as a way to “warn” India to stop acting aggressively on the border issue, Chinese Foreign Ministry spokesperson Wang Wenbin said, “As a staunch defender of cybersecurity, China firmly opposes and cracks down on all forms of cyberattacks.”
*** ***
The original report by nytimes.com : Context and the fine print
The original report by nytimes.com, Feb 28, needs to be looked into.
China Appears to Warn India: Push Too Hard and the Lights Could Go Out
With that sensational and provocative title, the report begins linking it to the conflict along the LAC thus:
“As border skirmishing increased last year, malware began to flow into the Indian electric grid, a new study shows, and a blackout hit Mumbai. It now looks like a warning…”
“But acknowledging its insertion, one former Indian diplomat noted, could complicate the diplomacy in recent days between China’s foreign minister, Wang Yi, and his Indian counterpart, Subrahmanyam Jaishankar, in an effort to ease the border tensions.”
This NYT report needs to be seen in the context of Biden’s tough-on-China policy.
See the scmp.com recent report below, independent of the current controversy.
Cybersecurity: Biden expected to embrace tough-on-China policy, think tank says
New US administration will continue strategic rivalry but there is room for cooperation, according to report by Chinese government-affiliated institute.
It also calls for a return to high-level talks on cyber issues such as digital trade, cross-border data flows and cybercrime
“There is room for cooperation”, between Biden’s US and China, says the report. So the NYT report keeps it open, speaking of only doubts.
India also is rethinking its China policy, as the latest agreement on de-escalation indicates.
It is all a fluid situation linked to possible policy shifts.
NYT report itself says: “ The flow of malware was pieced together by Recorded Future, a Somerville, Mass., company that studies the use of the internet by state actors. It found that most of the malware was never activated…”
“ Since then, Indian officials have gone silent about the Chinese code, whether it set off the Mumbai blackout and the evidence provided to them by Recorded Future that many elements of the nation’s electric grid were the target of a sophisticated Chinese hacking effort.
It is possible the Indians are still searching for the code, NYT said.
“And because Recorded Future could not get inside India’s power systems, it could not examine the details of the code itself, which was placed in strategic power-distribution systems across the country. While it has notified Indian authorities, so far they are not reporting what they have found.”
The investigators who wrote the Recorded Future study, said that “the alleged link between the outage and the discovery of the unspecified malware” in the system “remains unsubstantiated.”
While headlines scream China did the damage in Mumbai, fine print negates the same. As seen above, Indian Govt denied it.
NYT report itself quotes an Indian expert and says:
“I think the signaling is being done” by China to indicate “that we can and we have the capability to do this in times of a crisis,” said retired Lt. Gen. D.S. Hooda, a cyber expert who oversaw India’s borders with Pakistan and China. “It’s like sending a warning to India that this capability exists with us.”
So it did not happen, but they say they have a capability. But a Minister confirms conspiracy!
It is useful to recall what Hooda, a cyber expert quoted by NYT had said earlier, as reported by CC last year, June 9, 2020, under an apt sub-title, Indian Media Narrative Vs Reality.
See this prescient report titled India- China Border Tensions: A New Forward Policy?
“ The former Northern Army Commander, Lt. Gen. (retd) D.S. Hooda, said reports suggesting China had over the recent years “nibbled away” at parts of Indian territory were incorrect…
“In the past 15-20 years, there has been no real change in what we felt was the alignment of the LAC. Those [points] are sacrosanct to the Indian Army.”
“ Defence Minister Rajnath Singh, as if corroborating the above had said on June 02, 2020:
“There will hardly be a year when there is no face-off on the border between both the Indian Army and the Chinese Army. ”
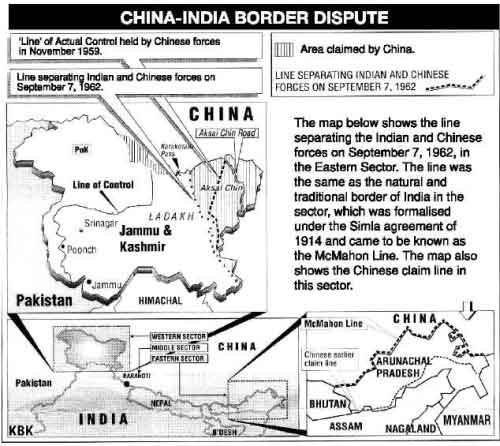
Former diplomat and expert of India, P.Stobdan went on record: “This is our Forward Policy…We will take Aksai Chin… This is not about LAC…. we have now become offensive…”
US has been aiding and abetting these policies as part of its Indo-Pacific strategy.
No real change in LAC, but soon Galwan clash happened, fortunately with no fire arms.
Now even as India and China agree on de-escalation, venomous reports are splashed to derail the peace process.
(https://countercurrents.org/2020/06/india-china-border-tensions-a-new-forward-policy/)
*** ***
The Hacker and the State: Cyberattacks and the New Normal of Geopolitics
The above is a headline of an article by an expert on the subject. The alleged events were by no means exclusive measures by China as against India. They are part of the New Normal of Geopolitics.
State secrets as well as economic secrets go together , and are accentuated with Trade wars US intensified, more so against China. Often hackers, both official and non-state actors, were reportedly attempting to steal data, part of spying, the oldest statecraft and business rivalries, now accentuated as trade wars.
A conversation with American Prof Ben Buchanan, author of The Cybersecurity Dilemma who recently published The Hacker and The State: Cyber Attacks and the New Normal of Geopolitics (Harvard University Press, 2020) was featured by thediplomat.com, March 24, 2020. Trans-Pacific View author, and senior media writer, Mercy Kuo engaged him in the conversation.
China broke the monopoly of super powers who were prying on it for decades. China turned the tables. So it came out. They are visible.
“While during the Cold War many espionage operations were hidden away by classification and other protections, in the modern age cyber operations are much more visible…”
“The case is striking not just because of the extent of the Chinese espionage operation but because it put hacking on the front pages of American newspapers, a place to which it would return with regularity in the years to come..”.
The United States and intelligence-sharing entities such as the Five Eyes are countering cyber espionage from China, Iran, North Korea, and Russia.
“They tell fascinating spy versus spy stories…There is a substantial industry of analysts with great visibility into how and why nations hack, and governments sometimes reveal the activities of their adversaries..”
“ It was a sign of how blurry the lines between espionage and counterespionage are in cyberspace and how fierce the competition between hackers and their states can be…”
How has hacking changed geopolitics?
This has got nothing to do with the alleged China’s hostility and rivalry with India. It is explained:
“ Hacking has quickly become a favored and powerful arrow in the quiver of statecraft. Over the last 20 years, a panoply of nations has found that hacking capabilities help them shape geopolitics to their liking. The result is a competition between government hackers that is fierce and nearly continuous; this competition is not unusual, reserved only for war time or extreme circumstances, but daily – it has become a key part of intelligence and military operations. From espionage to overt cyber-attacks to election interference and beyond, there is a lot that hackers can do in the service of their states.”
Both India and China maintain medium-size nuclear arsenals, as an ultimate deterrent, says the NYT, adding:
“Cyberattacks give them another option – less devastating than a nuclear attack, but capable of giving a country a strategic and psychological edge. Russia was a pioneer in using this technique when it turned the power off twice in Ukraine several years ago.”
“And the United States has engaged in similar signaling. After the Department of Homeland Security announced publicly that the American power grid was littered with code inserted by Russian hackers, the United States put code into Russia’s grid in a warning to President Vladimir V. Putin.”
“Now the Biden administration is promising that within weeks it will respond to another intrusion — it will not yet call it an attack — from Russia, one that penetrated at least nine government agencies and more than 100 corporations.”
So far, the evidence suggests that the SolarWinds hack, named for the company that made network-management software that was hijacked to insert the code, was chiefly about stealing information… Until recent years, China’s focus had been on information theft.
Thus it is all part of a cold war, in the form of Cyber tech-based warnings.
“ In the Indian case, Recorded Future sent its findings to India’s Computer Emergency Response Team, or CERT-In, a kind of investigative and early-warning agency most nations maintain to keep track of threats to critical infrastructure. Twice the center has acknowledged receipt of the information, but said nothing about whether it, too, found the code in the electric grid.
Repeated inquiries by The New York Times to the center and several of its officials over the past two weeks yielded no comment.
It is part of spying and intelligence, common to all major states across the world. NYT reports about Indian efforts:
“ The Chinese government, which did not respond to questions about the code in the Indian grid, could argue that India started the cyber aggression. In India, a patchwork of state-backed hackers were caught using coronavirus-themed phishing emails to target Chinese organizations in Wuhan last February. A Chinese security company, 360 Security Technology, accused state-backed Indian hackers of targeting hospitals and medical research organizations with phishing emails, in an espionage campaign.”
“One of the intentions seems to be power projection,” said Vineet Kumar, the president of the Cyber Peace Foundation.
‘Yet except for the Mumbai blackout, the attacks have not disrupted the provision of energy, officials said. (About Mumbai, India officially denied China’s role, as seen above.)
“ And even there, officials have gone quiet after initially determining that the code was most likely Chinese. Yashasvi Yadav, a police official in charge of Maharashtra’s cyber-intelligence unit, said authorities found “suspicious activity” that suggested the intervention of a state actor. But Mr. Yadav declined to elaborate, saying the investigation’s full report would be released in early March.”
The mischievous play of words by NYT is notable: “initially determining”; later it reports “suspicious activity”…and “officials have gone quiet.”
“I think the signaling is being done” by China to indicate “that we can and we have the capability to do this in times of a crisis,” said retired Lt. Gen. D.S. Hooda, a cyber expert who oversaw India’s borders with Pakistan and China. “It’s like sending a warning to India that this capability exists with us.” (NYT report)
The alleged capability is shown as an act committed.
“Misinformation refers to false or out-of-context information that is presented as fact regardless of an intent to deceive. Disinformation is a type of Misinformation that is intentionally fals and intended to deceive or mislead.”
Both are promoted in a rampant manner, so as to manufacture consent …by ruling classes. Big Media is their handmaid in this.
***
China firmly cracks down on all forms of cyberattacks: Chinese Embassy in India
A Chinese embassy statement on March 1 said that the country does not support cyber attacks.
“China firmly opposes and cracks down on all forms of cyber attacks. Speculation and fabrication have no role to play in the issue of cyberattacks. Highly irresponsible to accuse a particular party with no sufficient evidence around,” said Chinese Embassy spokesperson. (timesofindia.com , March 1), 2021.
Then comes the real business war, and related lobbying, at the end of the NYT report:
“Military experts in India have renewed calls for the government of Prime Minister Narendra Modi to replace the Chinese-made hardware for India’s power sector and its critical rail system.
“The issue is we still haven’t been able to get rid of our dependence on foreign hardware and foreign software,” General Hooda said:
“Indian government authorities have said a review is underway of India’s information technology contracts, including with Chinese companies. But the reality is that ripping out existing infrastructure is expensive and difficult.”
So, all this misinformation and disinformation has a business motive. There is nothing unfair in love and business. But the gullible common man is confounded. Patriotism is the last resort of a scoundrel.
(For full NYT report, see: https://www.nytimes.com/2021/02/28/us/politics/china-india-hacking-electricity.html)
*** ***
Misinformation is quite common, whenever peace is being negotiated
Counter currents had published a series of reports last year on India China LAC conflict. It is instructive to recall some facts. It also cited how, playing spoil sport, the NYT had published a Report. It is worth recounting the reports in CC.
Indian Army had to issue a fact-checker exposing “fake news” in May last year
Flood of Misinformation on the eve of India China Talks was the title of a report the CC had published June 5, 2020.
Misinformation and disinformation are quite common, more so whenever peace talks are in the news. Last year, before the Galwan’s clash which without fire arms, and which was during a process of de-escalation, the Indian military had to issue a clarification exposing “fake news” that was “malafide.”
The Indian Army itself on May 31 last year rejected a video, which emerged on the social media, purportedly showing clashes between Chinese and Indian troops in eastern Ladakh.
The video being circulated is fake, the PIB had said, and mala fide.
“The contents of video being circulated are not authenticated. Attempt to link it with the situation on the Northern borders is mala fide,” the Army said in a statement. The Govt info buro, the PIB itself had issued a fact-checker that refuted the stories catching headlines.
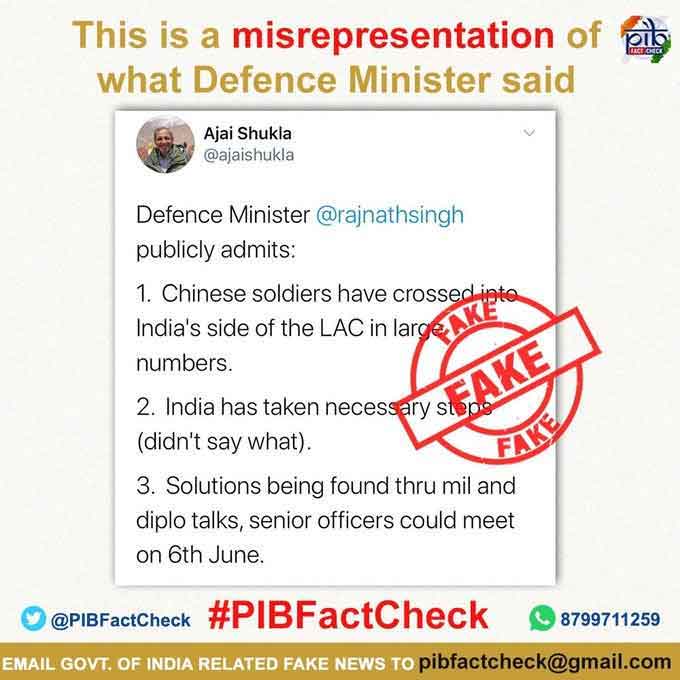
“We strongly condemn attempts to sensationalise issues impacting national security. The media is requested not to air visuals that are likely to vitiate the current situation on the borders,” it added.
Despite the above fact checker by the Army itself, misinformation by media was rampant.
After India- China “Agreed to peacefully resolve the situation in the border areas”, as CC reported June 8, 2020, attempts were made to derail them.
“As someone who has seen this situation developing over the past 50-60 years,” former national security advisor (NSA) of India. M.K. Narayanan (on May 29) urged caution when looking at the current Indo-Chinese stand-off…..
“I was there in 1959, 60, 61, 62 — the two sides try to play chess at the border … but to use the term ‘military stand-off’ is too much. As someone who has seen this situation developing over the past 50-60 years, we should see issue firmly and coolly,” said Narayanan, who had also served as the chief of the Intelligence Bureau and Joint Intelligence Committee.
According to the former national security adviser (NSA), who held discussions with his Chinese counterparts, the key problem with the India-China border is that it is un-demarcated and undefined….It happens that we have our perception and China has their own…” he said.
Talks Concluded : Times of India June 7 reported :
“…sources said the meeting was “positive” and could eventually lead to restoration of status quo ante in eastern Ladakh, with both sides de-inducting soldiers and heavy weaponry from the confrontation sites at the northern bank of Pangong Tso (Tso means lake), Gogra-Hot Springs area and Galwan Valley region in a phased manner.
The Hindu June 7 additionally referred to media role:
Before the talks began, the Army issued an advisory to the media that both sides remained engaged through established military and diplomatic channels “to address the current situation in the India-China border areas” and speculation would not be helpful. “At this stage, therefore, any speculative and unsubstantiated reporting about these engagements would not be helpful and the media is advised to refrain from such reporting,” it said.
Former Indian Army chief General Bikram Singh on June 6 :
“It may get resolved today. But if not today, it may take two-three more meeting…This is a very opportune time to get a permanent solution to this issue because both countries are presently headed by strong leaders. I had said this some years back in a column too,”
He said border disputes with China is a vexed issue because parliaments of both the countries have stated that the disputed territory is theirs. “But it can be resolved with a strong political leadership. It (border dispute) will have to be made a national issue that needs to be resolved.“
The former army chief however said a final solution to the border dispute with China can be reached only at the political and diplomatic level.
Speaking about the Indian Army’s preparedness, he added: “At present, we should not indulge in things that can raise temperature and escalate the situation.”
That was what US agencies attempted. Playing spoil sport, the NYT Report post-talks had then said:
“China appeared to have stepped up its activity in the area this spring after the recent expansion of a road network on the Indian side of the border. India has been trying to strengthen its defenses in the remote region, where altitudes exceed 14,000 feet.”
Then came Galwan clash.
Similar disinformation is happening now as Defence Minister Rajnath Singh on Feb 11 announced in Parliament that India and China have reached an agreement on disengagement along the LAC.
Countercurrents recently published an article, almost like a warning of things to come:
Indian army has a strong US lobby, it is well known, as MK Bhadrakumar, former diplomat stated. In an aptly titled comment , (India’s forever wars and forever warriors) about Indian hawks aided and abetted by USA, wrote in his blog on February 19:
“No doubt, the decision is in India’s national interests,” said former diplomat M K Bhadrakumar,” the( Indian) government decided to prioritise peace and tranquility on a sustainable basis.”
The US welcomed the ongoing efforts by India and China to de-escalate the situation, reported PTI, Washington , on feb 12, 2021. But that was only for the record, as can be seen below.
Bhadrakumar wrote:
“Why do Indian analysts look crestfallen? Fundamentally, the adversarial mindset inculcated through decades of indoctrination since 1962 explains it. As happens in opaque circumstances, interest groups proliferate, like mushrooms in damp soil.
“ Clearly, India and China have a lot of ground to cover to reach the ‘October 2003 moment’ in their relationship. The US will not probably countenance such a moment, either, as sans India, its Indo-Pacific strategy will remain a damp squib.
Nor is India’s foreign-policy trajectory leaning toward a quasi-alliance with the US going to be helpful.
Suffice to say, India also has a powerful pro-American lobby clamouring for “forever wars”.
Sinophobia feeds into it seamlessly. This lobby will only gain ascendancy, as India develops a defence industry and the corporate interests and their eventual nexus with the defence establishment come into full play, inevitably, in the domain of foreign and security policies.
Thus, the ‘forever warriors’, being the best organised and best-endowed faction — and highly motivated too — almost always prevails, in the final analysis.
https://countercurrents.org/2021/02/indias-forever-wars-and-forever-warriors/
“The US will not probably countenance such a moment, either, as sans India, its Indo-Pacific strategy will remain a damp squib”, the seasoned diplomat wrote.
Thus in his blog February 19, he anticipated hurdles from the and highly motivated hawks, who are adept in misinformation and disinformation.
And the NYT Report indeed appeared on Feb 28. And it is relayed, echoed in multiple decibels, by the Indian big media.
*** ***
After almost an year of anti-China tirade, about China’s alleged aggressive actions, about which US agencies also spread canards, the reality has come out, from the horse’s mouth.
“The stunning disclosure recently by Minister VK Singh, a former army chief, that Indian ingressions must be five times the number of Chinese ingressions historically, underscores the criticality of buffer zones…
“VK Singh’s disclosure is a rare acknowledgement of ground realities which successive governments through past decades obfuscated as a matter of political expediency..”
Bhadra Kumar was referring to the remarks Singh made on 7th Feb. The former army chief also said “The border with China has never been demarcated”.
Dr S Jatin Kumar , on February 18, 2021, an office-bearer of India China Friendship Association, quoted singh and raised the question:
“China has transgressed many times over the years with its own perception of the LAC. Similarly, none of you come to know how many times we have transgressed as per our perception. Chinese media does not cover it” said the former army chief.
The same was echoed when our PM Modi categorically told all party leaders through his video conference on June 9thlast year that “neither is anyone inside our territory nor is any of our post captured”.
If nobody intruded into our land, then why every citizen is fed with a dubious information that Chinese have occupied our land.
It is worth recalling what Subramanian Swamy, Sinologist, Ex-Union Minister, and BJP MP had said:
“ China has borders with 14 nations, and except for India, it has resolved its disputes with all, including Russia. India has borders with six countries, and excluding Bhutan, it has disputes with all five.”
(Frontline 2000 Sep 2: Sino-Indian Relations Through the Tibet Prism)
The above is reiterated 20 years later even by a hawkish official recently:
“China shares its borders with 14 countries — they have delineated boundaries with 12 of those countries, the only two countries they haven’t settled boundaries with are India and Bhutan.
“Until and unless we demarcate boundaries, the problem will remain. We haven’t exchanged maps and our understanding of the boundary is perception based.” (Former General Sanjay Kulkarni)
Obviously India did not basically change its policy in 20 years under UPA and NDA.
After 45 years when not a bullet was fired along the LAC, as admitted officially, they could inflame the Galwan incident, again with no fire arms, an avoidable tragedy. But patriotism and jingoism call for sacrifices. Now we see how Jai Kisan is exposed. We need to expose Jai Jawan too, how they are reduced into cannon fodder to serve merchants of death, the war industry.
After all we have to push up the GDP, come what may. The govt has opened up Defence for 100 percent FDI. Private sector majors are waiting to reap the benefits.
Ambanis and the like should top the table of billionaires, even as India falls below in several rankings like HDI.
People have to make sacrifices. Jawans and kisans too.
Cyber Attack On India’s Power Utilities?
No it is an imperialist onslaught on India-China peace efforts.
Peace is more difficult to win than a war. But people need peace and development while rulers’ needs are otherwise: For them, peace is the time between two wars.
***
Ramakrishnan is a journalist
GET COUNTERCURRENTS DAILY NEWSLETTER STRAIGHT TO YOUR INBOX